Introduction to CKKS
cryptography
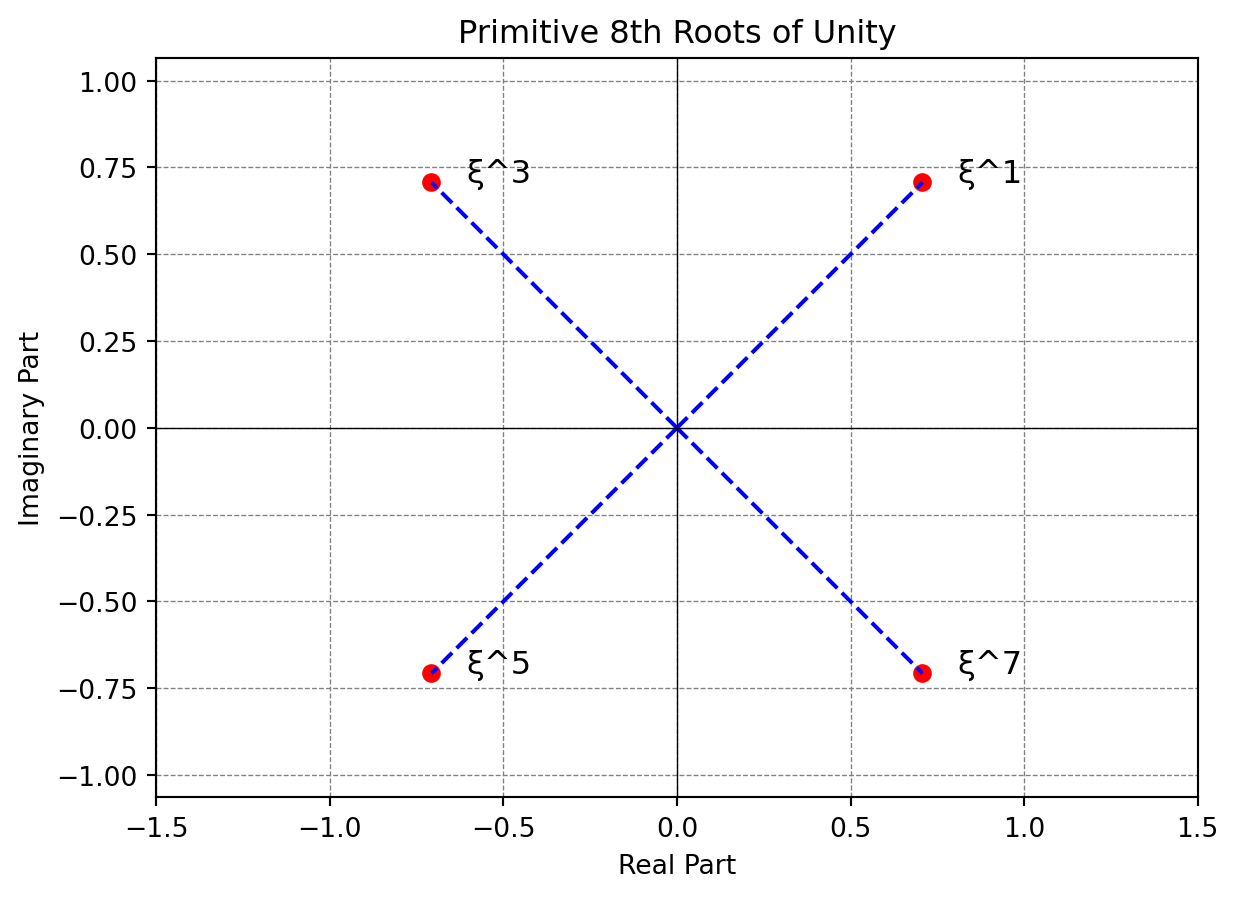
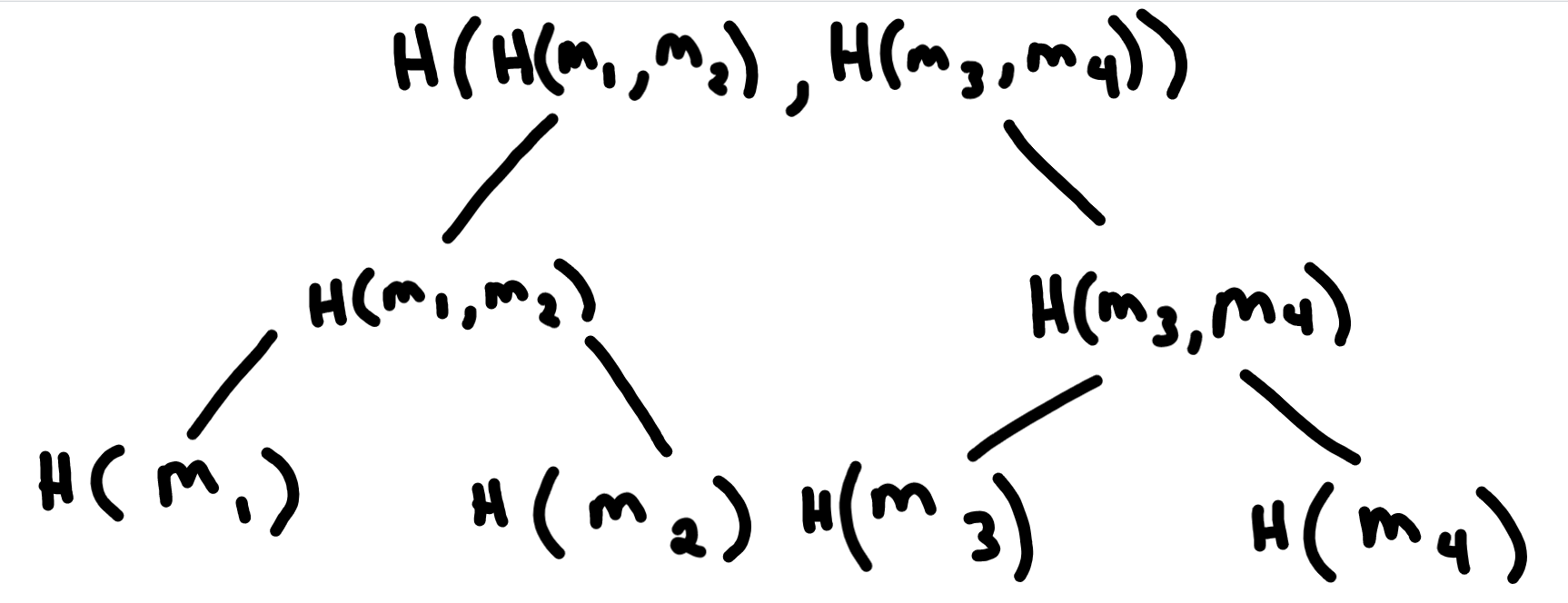
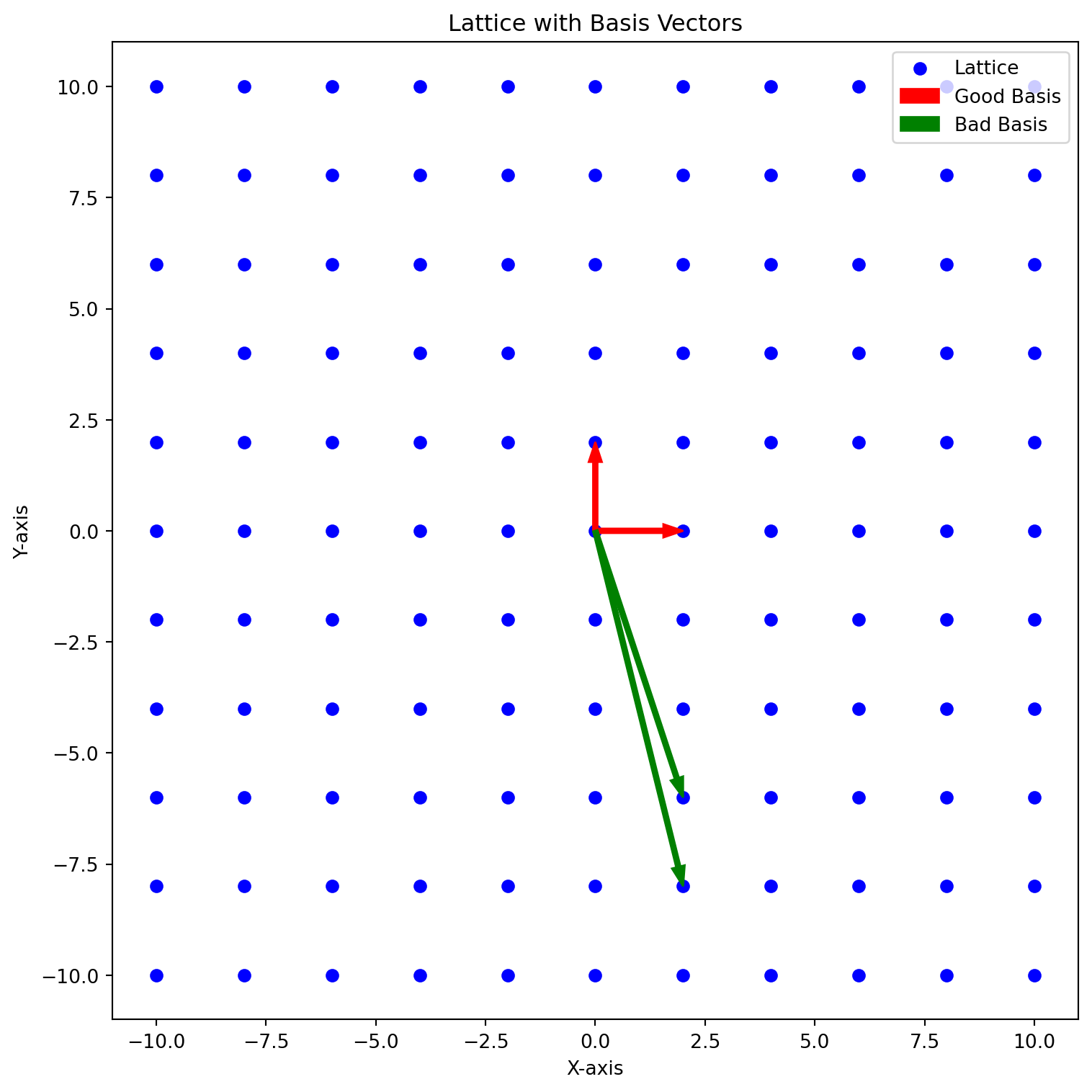
The HEAAN / CKKS scheme introduced in the paper, Homomorphic Encryption for Arithmetic of Approximate Numbers or named after the authors, Jung Hee Cheon, Andrey Kim, Miran Kim, and Yongsoo Song is a leveled homomorphic scheme based upon the Ring Learning with Errors (RLWE) problem…
No matching items